Security Alerts
** Please be aware that documents from these alerts may contain links that connect you to other websites. The First is not responsible for the content on other sites. Other websites may treat information they learn about you differently.
February 26, 2024 - Beware of Fraud Attempts
We have reports of a phishing scam that has been targeting bank customers. The suspicious text messages claim that your account is on hold. They contain numerous misspellings and punctuation errors. These messages are designed to trick you into revealing personal information or clicking on malicious links.
It’s crucial to stay vigilant and recognize the signs of phishing attempts. One common red flag is the presence of misspellings and grammatical errors in the messages. Legitimate communications from our bank are carefully crafted and thoroughly proofread, so any message containing noticeable errors should raise immediate suspicion.
Your security is our top priority, and we want to ensure that you feel confident and informed when it comes to protecting your financial information. If you receive any suspicious messages, emails, or calls claiming to be from our bank, please do not hesitate to contact your nearest branch immediately.
Remember, never provide personal or sensitive information in response to unsolicited communications, and always verify the legitimacy of any requests before taking action. By staying vigilant and cautious, we can work together to safeguard your accounts and financial well-being.
If you have any concerns or questions regarding the recent phishing scam or any other security-related matters, please don’t hesitate to reach out to us. We’re here to help you navigate through any challenges and ensure a safe banking experience for all our customers.
August 7, 2023 - Beware of Phishing Scams
This post is to inform you of a recent increase in phishing scams targeting our customers. Phishing is a fraudulent attempt to obtain your personal or financial information, such as passwords, account numbers, or credit card details, by pretending to be a legitimate entity. Phishing can occur through email, text message, phone call, or other means.
We urge you to be vigilant and protect yourself from these scams. Here are some tips to help you identify and avoid phishing:
– Do not open or respond to unsolicited emails or text messages that ask you to verify your account, update your information, or claim that there is a problem with your payment.
– Do not click on any links or attachments in suspicious emails or text messages. They may lead you to fake websites that look like ours, but are designed to steal your information.
– Do not provide any personal or financial information over the phone, unless you initiated the call and verified the identity of the person you are speaking to.
– Always check the sender’s address and the URL of the website you are visiting. Make sure they match our official domain name and email address.
– If you receive a phishing email or text message, please report it to us immediately by forwarding it to security@fnbn.com
We take your security seriously and we are working hard to prevent and stop these scams. However, we cannot do it alone. We need your cooperation and awareness to keep your account safe.
Thank you for choosing The First and trusting us with your business.
May 31, 2022 - Intuit warns of QuickBooks phishing threatening to suspend accounts
Tax software vendor Intuit has warned that QuickBooks customers are being targeted in an ongoing series of phishing attacks impersonating the company and trying to lure them with fake account suspension warnings.
Today’s alert comes after Intuit received multiple user reports who received these phishing emails and notified their QuickBooks accounts were suspended following a failed business info review.
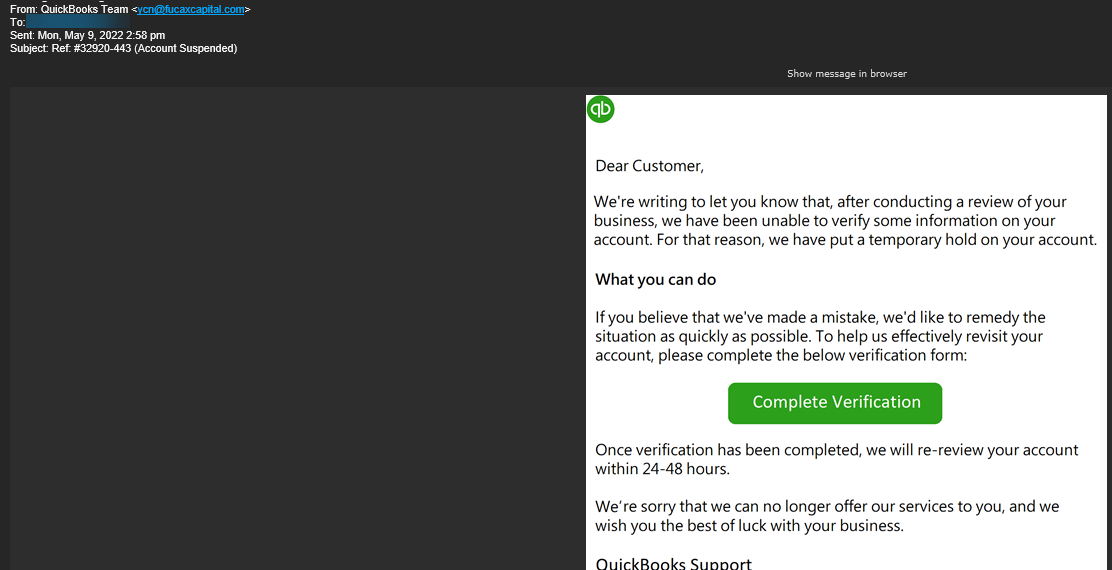
“We’re writing to let you know that after conducting a review of your business, we have been unable to verify some information on your account. For that reason, we have put a temporary hold on your account,” the attackers say in the phishing messages while impersonating the QuickBooks support team.
“If you believe that we’ve made a mistake, we’d like to remedy the situation as quickly as possible. To help us effectively revisit your account please complete the below verification form. Once verification has been completed, we will re-review your account within 24-48 hours.”
Clicking the “Complete Verification” button in the phishing email will likely redirect the recipients to a landing phishing site designed to harvest their personal information or infect their systems with malware.
The accounting software maker also added that the sender “is not associated with Intuit, is not an authorized agent of Intuit, nor is their use of Intuit’s brands authorized by Intuit.”
How to make sure you’re not phished
Intuit advises customers who received one of these phishing messages not to click any embedded links or open attachments.
It also recommends deleting them from the inbox to avoid getting infected with malware or sent to some phishing landing page under the attacker’s control that would attempt to harvest the targets’ credentials.
QuickBooks users who have already opened attachments or clicked links after receiving one of these phishing emails should:
- Delete any downloaded files immediately.
- Scan their systems using an up-to-date anti-malware solution.
- Change their passwords.
Intuit also provides detailed info on how customers can protect themselves from phishing attempts on its support website.
Earlier this year, in February, Intuit warned QuickBooks customers they were the targets of a phishing campaign impersonating the company and threatening to delete their accounts.
September 23, 2021 - Reducing the Risk of Fraud on the Zelle Network®
The First National Bank and Trust Co. of Newtown actively works to reduce the risk of fraud on the Zelle Network®, however, the recent health concerns that have impacted every aspect of our lives have led consumers to increasingly turn to digital payments, enabling fraudsters to hide among the larger volume. These fraudsters are taking advantage of the pandemic, using fear and uncertainty to victimize consumers.
The purpose of this bulletin is to notify you of a social engineering scam that has been observed across multiple social payment applications, including Zelle®, and to remind you of the need for continued vigilance to protect your Zelle® account.
Social Engineering Scam
In one scenario, the consumer receives a text from a fraudster to alert about a suspicious transaction. Upon receiving a response text declining the transaction from the consumer, the fraudster calls the consumer, pretending to be the fraud department of the financial institution. The fraudster gains access to the consumer’s online banking account by requesting the username and one-time password, which is then used to reset the password. Upon gaining access to the online account, the fraudster registers for Zelle® and attempts to send payments.
In most of these cases, our risk models detect the fraud activity and the transactions as high risk. The user then receives a stepped-up authentication request via SMS (text) to authorize the payment. Through social engineering and direct calls, some users are still falling victim to these fraud scams. In these cases, the fraudster calls to convince the consumer to authorize the stepped-up authentication request, so that the consumer can receive a refund from the previously fraudulent transaction. In reality, the consumer is not getting a refund, but is sending the payment to the fraudster.
Remember:
- FNBN will never call you to request information you received via text (SMS) or pressure you to reset your online banking log in password
- Don’t trust caller ID; Caller ID may be modified to show FNBN’s name
- Don’t provide your online banking log in credentials, one-time password, account number or personal information by email or text or phone call. Instead, reach out to FNBN to confirm that the request is legitimate by calling us at 215-860-9100
- Don’t give information over the phone if you receive a call stating that a transaction is canceled, even if the caller claims to be from FNBN. Once again, contact us directly by phone at 215-860-9100 to inquire about the transaction
- Don’t click on links in unsolicited emails or texts
- Don’t give an unsolicited caller remote access to your computer
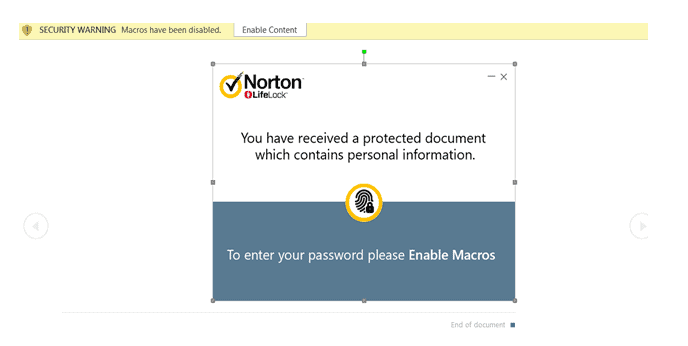
March 3, 2021 - Norton 360 LifeLock Scam
The scam begins with a phishing email, which appears to be from the anti-virus and software security company. The email which has an attachment containing malicious macros informs the recipient that they have received a protected document from Norton LifeLock. To access the document, the recipient is provided a password and is instructed to enable macros.
Such trojans are often concealed as an anti-virus program, tricking the user into installing it onto their device. Once installed, the trojan then works quietly in the background to steal sensitive data, install a backdoor or take other harmful actions. RATs can be difficult to detect because they often do not appear in the list of the programs running on the device and nor do they affect your device’s performance.
When the user inputs the correct password to access the spoof document, the macro executes a command to install the remote access trojan, giving the cybercriminals free rein to the victim’s machine. Before the script continues its operations, it checks to see if an anti-virus is installed on the system. If this is the case, it stops running on the victim’s computer.
With this access, hackers can then monitor online behaviors, access confidential information, format computer drives, distribute viruses, delete or alter files and even watch the victims via their webcams to use for blackmail or ransom.
How to protect against phishing
With 90% of all data breaches caused by phishing and 3.4 billion fake emails sent every day, users must remain cautious and vigilant. Educating yourself, your staff, and your end users about phishing can significantly minimize your risk. To stay safe, there are a number of simple ways you can protect yourself from such attacks:
- Never click on links or download attachments from unknown sources.
- Ensure that all applications and operating systems are up to date.
- Hover your mouse over the links contained in emails to check if they are legitimate– don’t click unless you are sure they are safe.
- Install the latest anti-virus software solutions on all your devices.
- Use strong passwords to reduce the chance of devices being hacked and use different passwords for different accounts.
- Install a Firewall to prevent unauthorized access to your network.
- Back up data on a regular basis.
- Question the validity of any email that asks you to submit personal or financial information.
Source: MetaCompliance
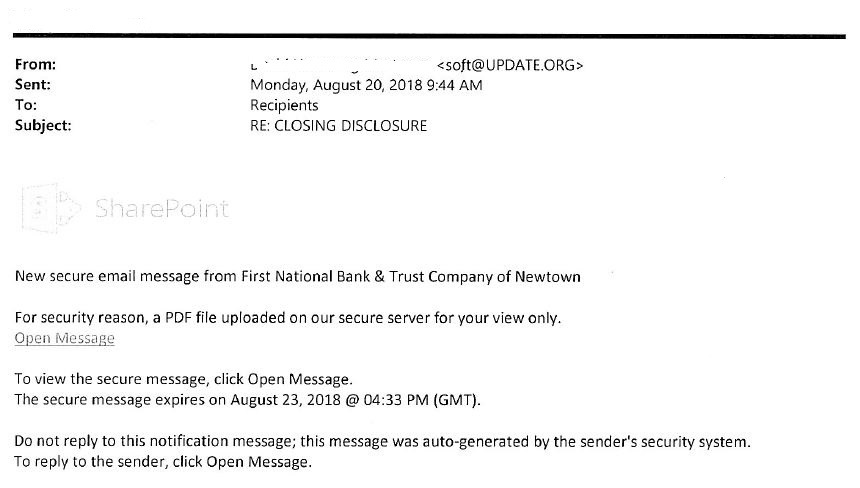
August 21, 2018 - Spam Email Reportedly from The First
Customers have reported receiving the email below which supposedly was sent from “First National Bank & Trust Company of Newtown.” However, the from address is soft@UPDATE.ORG. Please be advised that this email did not originate from The First National Bank. We highly recommend for security reasons to never click any link or open any attachment from an email that you were not expecting. If you have any question about an email from The First, please contact your branch or call us at 215-860-9100.
June 7, 2018 - Foreign Cyber Actors Target Home and Office Routers and Networked Devices Worldwide
Summary
The FBI recommends any owner of small office and home office routers power cycle (reboot) the devices. Foreign cyber actors have compromised hundreds of thousands of home and office routers and other networked devices worldwide. The actors used VPNFilter malware to target small office and home office routers. The malware is able to perform multiple functions, including possible information collection, device exploitation, and blocking network traffic.
Technical Details
The size and scope of the infrastructure impacted by VPNFilter malware is significant. The malware targets routers produced by several manufacturers and network-attached storage devices by at least one manufacturer. The initial infection vector for this malware is currently unknown.
Threat
VPNFilter is able to render small office and home office routers inoperable. The malware can potentially also collect information passing through the router. Detection and analysis of the malware’s network activity is complicated by its use of encryption and misattributable networks.
Defense
The FBI recommends any owner of small office and home office routers reboot the devices to temporarily disrupt the malware and aid the potential identification of infected devices. Owners are advised to consider disabling remote management settings on devices and secure with strong passwords and encryption when enabled. Network devices should be upgraded to the latest available versions of firmware.
September 7, 2017 - Equifax Announces Cybersecurity Incident Involving Consumer Information
September 7, 2017 — Equifax Inc. (NYSE: EFX) today announced a cybersecurity incident potentially impacting approximately 143 million U.S. consumers. Criminals exploited a U.S. website application vulnerability to gain access to certain files. Based on the company’s investigation, the unauthorized access occurred from mid-May through July 2017. The company has found no evidence of unauthorized activity on Equifax’s core consumer or commercial credit reporting databases.
The information accessed primarily includes names, Social Security numbers, birth dates, addresses and, in some instances, driver’s license numbers. In addition, credit card numbers for approximately 209,000 U.S. consumers, and certain dispute documents with personal identifying information for approximately 182,000 U.S. consumers, were accessed. As part of its investigation of this application vulnerability, Equifax also identified unauthorized access to limited personal information for certain UK and Canadian residents. Equifax will work with UK and Canadian regulators to determine appropriate next steps. The company has found no evidence that personal information of consumers in any other country has been impacted.
Equifax discovered the unauthorized access on July 29 of this year and acted immediately to stop the intrusion. The company promptly engaged a leading, independent cybersecurity firm that has been conducting a comprehensive forensic review to determine the scope of the intrusion, including the specific data impacted. Equifax also reported the criminal access to law enforcement and continues to work with authorities. While the company’s investigation is substantially complete, it remains ongoing and is expected to be completed in the coming weeks.
“This is clearly a disappointing event for our company, and one that strikes at the heart of who we are and what we do. I apologize to consumers and our business customers for the concern and frustration this causes,” said Chairman and Chief Executive Officer, Richard F. Smith. “We pride ourselves on being a leader in managing and protecting data, and we are conducting a thorough review of our overall security operations. We also are focused on consumer protection and have developed a comprehensive portfolio of services to support all U.S. consumers, regardless of whether they were impacted by this incident.”
Equifax has established a dedicated website, www.equifaxsecurity2017.com, to help consumers determine if their information has been potentially impacted and to sign up for credit file monitoring and identity theft protection. The offering, called TrustedID Premier, includes 3-Bureau credit monitoring of Equifax, Experian and TransUnion credit reports; copies of Equifax credit reports; the ability to lock and unlock Equifax credit reports; identity theft insurance; and Internet scanning for Social Security numbers – all complimentary to U.S. consumers for one year. The website also provides additional information on steps consumers can take to protect their personal information. Equifax recommends that consumers with additional questions visit http://www.equifaxsecurity2017.com/ or contact a dedicated call center at 866-447-7559, which the company set up to assist consumers. The call center is open every day (including weekends) from 7:00 a.m. – 1:00 a.m. Eastern time.
In addition to the website, Equifax will send direct mail notices to consumers whose credit card numbers or dispute documents with personal identifying information were impacted. Equifax also is in the process of contacting U.S. state and federal regulators and has sent written notifications to all U.S. state attorneys general, which includes Equifax contact information for regulator inquiries.
Equifax has engaged a leading, independent cybersecurity firm to conduct an assessment and provide recommendations on steps that can be taken to help prevent this type of incident from happening again.
CEO Smith said, “I’ve told our entire team that our goal can’t be simply to fix the problem and move on. Confronting cybersecurity risks is a daily fight. While we’ve made significant investments in data security, we recognize we must do more. And we will.”
September 15, 2016 - IRS Impersonation Scam
Please be advised, the IRS will not contact you by phone with threats for non-payment of tax liability. The IRS does not require Green Dot, iTunes, Amazon.com, Moneypak or any other kind of gift card or credit card for tax payment. Beware of IRS Impersonation Scams – Just hang up! For more information or to report scams go to: http://www.tigta.gov
February 23, 2016 Texting Scam
A number of customers and non-customers have received a fraudulent text message showing an 800 number or a hyperlink that looks like it goes back to their account. These numbers or links are not associated with The First and are a scam. If you have any questions about a text message you may have received, please contact our Bank at 215-860-9100.
January 7, 2016 Phishing Scam
Our Bank would never contact our customers asking for their debit card or pin number. If you receive a call, do not give out any information. This is most likely a phishing attempt to obtain your card and pin information. If you have any questions about a call you may have received, please contact our Bank immediately at 215-860-9100.
Bucks County Sheriff's Department warning residents of phone scam - April 13, 2015
DOYLESTOWN >> The Bucks County Sheriff’s Office has received numerous complaints from residents who have received phone calls from someone claiming to be a Bucks County Sheriff’s Deputy.
The phone caller states that he or she has a warrant for them and if they don’t pay a certain amount of money they will be arrested. At that point, the caller asks for the person to meet them in a shopping center parking lot.
“This phone call is a scam,” said Bucks County Sheriff Edward Donnelly.
“The Bucks County Sheriff’s Office would never call and ask for money,” Sheriff Donnelly said. “Our office also would never ask to meet a subject in a shopping center lot.”
Anyone who receives a phone call of this nature should hang up immediately and contact the Bucks County Sheriff’s Office at 215-348-6123 or call the local police department.
"Heartbleed" OpenSSL Vulnerability - April 9, 2014
A group of security researchers uncovered a major vulnerability in the encryption technology used by millions of websites. Called “Heartbleed”, it is a security flaw found in OpenSSL, which is used to protect sensitive data such as emails, passwords or credit card data.
The First does NOT use OpenSSL and therefore is not affected by this discovery.
However, it is estimated that nearly two thirds of websites on the Internet use OpenSSL in some way. Any secure information on those sites such as passwords, email addresses, etc. could be compromised. The First National Bank always recommends that your online banking password is a unique password that you have never used on any other website.
Also, we recommend changing your online banking password on a regular basis.
If you have any questions, please feel free to contact the Online Banking Department at 215-579-3415.
PHISHING SCAM Alert - February 18, 2014
It has been reported to The First National Bank that some of our customers have received the following text message: Due to suspicious activity, your debit card has been temporarily blocked. In order to unlock, PLEASE call us immediately at: 1-713-988-6565. This is a scam. The First National Bank will never text or call you asking for your account information. If you have received one of these calls or texts, please report it to us immediately at 215-860-9100.
Data Breach at a Target® - December 20, 2013
Attention Debit Card Users: As you have seen in the news, there was a data breach at Target® possibly affecting millions of debit and credit card users. The breach occurred from 11/27/13 through 12/15/13. Please check your account transactions. If you see anything unusual please contact our Customer Call Center at: 215-860-6351. First National Bank is working closely with our debit cardholders that were affected.
Update as of 12/24/13: FNB is in the process of reissuing all debit cards affected by the Target store compromise. New cards should arrive in 7-10 business days. Please continue to check your account transactions. If you see anything unusual, contact our Customer Call Center at: 215-860-6351.
Organized Crime Ring in our Area - October 1, 2012
Please be aware that a group of criminals, commonly referred to as “The Felony Lane Gang” has been active in our area. Originating in Florida, this group preys on purses that have been left unattended in a vehicle. Common areas include, sports events, gyms, cemeteries and elementary schools. After breaking into the vehicle, the gang will facilitate fraud while assuming the identity of the victim. If you become the victim of this crime, please notify us at 215-860-9100.
PHISHING SCAM Alert - February 28, 2012
It has been reported to First National Bank that some of our customers have received cell phone calls or text messages from someone claiming to be from First National Bank. This is a scam. First National Bank will never text or call you asking for your account information. If you have received one of these calls or texts, please report it to us immediately at 215-860-9100.
MASQUERADING WEB SITE Alert - November 17, 2011
The Office of the Comptroller of the Currency (OCC) has been informed that the Web site, “helpwithmybank.com,” is attempting to masquerade as the legitimate Web site, “helpwithmybank.gov,” and contains potentially damaging malware. The illegitimate site redirects the user to the legitimate site “helpwithmybank.gov” in an attempt to convince users that they are connecting to a legitimate site. Attempts to connect to the fake Web site could expose the user to harmful malware.
NACHA Alert - March 31, 2011
NACHA, the not-for-profit Association that governs electronic movement of money and data, like direct deposits and debit card transactions, has issued an alert concerning fraudulent emails. These emails, appearing to be from NACHA may ask for your personal information so that they can steal your identity, or ask you to open an attachment that will place a virus on your computer. Click on the link below to read NACHA‘s statement. If you think you may have become victim to this scheme, please call us today.
http://www.nacha.org/news/newsDetail.cfm/RecentBusinessNewsID/207
Email Fraud Alert - January 31, 2011
The First wants you to be aware of a phishing scam email that was received by one of our customers. The email directed the customer to visit a malicious site and download and install a piece of software. Below is the text of the email.
Subject: A NOTE FROM FNB Due to the recent Malware and Phishing attacks encountered by our customers, First National Bank has made it mandatory to all Customers to download the Rapport Software that will help fight against it. Our system shows that you have not downloaded the latest version of this software that was introduced on 17-01-2010. It is your responsibility to protect your account by installing this new patch as a precautionary measure. If you do not log on to download this software now, First National Bank will not be liable for any theft that may occur on your account.
If you receive this email, or any email similar to it, please delete it immediately. Do not click any links within the email, and do not reply to it.
The First does not:
- Send emails regarding account deactivation, account lockouts, or other problems.
- Send emails asking you to provide, update or verify your personal, business, account or other confidential information.
FDIC Reports Fraudulent E-mails Claiming To Be from Agency - January 13, 2011
The FDIC said that it has received numerous reports from consumers of fraudulent e-mails that appear to have come from the FDIC. The e-mails say that the FDIC in cooperation with the Department of Homeland Security has withdrawn the recipients’ deposit insurance “due to account activity that violates the Patriot Act.”
It says that deposit insurance will remain suspended until identity and account information can be verified using a system called “IDVerify.” If consumers go to the link provided in the e-mail, it is suspected they will be asked for personal or confidential information, or malicious software may be loaded onto the recipient’s computer. Financial institutions and consumers should not access the link provided within the body of the e-mail and or provide any personal information through this media. Read FDIC Alert.
Email Fraud Alert - June 9, 2010
The First wants you to be aware of an email-based scam that attempts to collect confidential and financial information. These scams are often referred to as “phishing.”
A phishing email has been sent out that fraudulently states that your account is being blocked and that you are required to update or verify your account information by clicking a link that takes you to a fake login site. Do not click the link in the email as the website you are taken to is not a website of The First, but rather a fraudulent website made to look like the Online Banking login page.
The First does not:
- Send emails regarding account deactivation, account lockouts, or other problems.
- Send emails asking you to provide, update or verify your personal, business, account or other confidential information.
What to Do if you entered information on the Fraudulent Site:
If you have entered personal information after clicking on the link or suspect fraudulent behavior, please call us immediately at (215) 860-9100 or contact your local branch. If you have received a fraudulent email, please forward it to onlinebankingmanager@fnbn.com. Please do not remove the original subject line, or change the email in any way when you forward it to us.
The First National Bank and Trust Company of Newtown’s Public Website Defaced - May 5, 2010
Between approximately 7:30 pm and 10:00 pm on Wednesday, May 5th our public website that is hosted at our Internet service provider was defaced by a hacker. The website displayed a message that said “Hacked By GhoST61” and a picture of the first President of Turkey. This did not infect our secure online banking server which is housed at the bank. Customers saw the “hacked” message after they exited from Online Banking and were directed back to our public website or by visit our public website directly. There was no account information compromised during the incident as the secure server which contains that information was not penetrated. Likewise the screen that customers saw did not indicate that there is anything wrong with their computers. The defacing did not transmit a virus or any malicious software onto any customer’s computer.
We apologize for the concern and inconvenience that this caused our customers. If you have any further questions, feel free to contact the Online Banking Manager at 215-579-3415.
Haitian Earthquake Relief Scams - January 14, 2010
The Federal Bureau of Investigation has posted a warning regarding possible Haitian earthquake relief scams. The FBI reminds internet users who receive appeals to donate money in the aftermath of Tuesday’s earthquake in Haiti to apply a critical eye and do their due diligence before responding to those requests. Past tragedies and natural disasters have prompted individuals with criminal intent to solicit contributions purportedly for a charitable organization and/or a good cause. Therefore, before making a donation of any kind, consumers should adhere to certain guidelines, to include the following:
- Do not respond to any unsolicited (spam) incoming e-mails, including clicking links contained within those messages.
- Be skeptical of individuals representing themselves as surviving victims or officials asking for donations via e-mail or social networking sites.
- Verify the legitimacy of nonprofit organizations by utilizing various Internet-based resources that may assist in confirming the group’s existence and its nonprofit status rather than following a purported link to the site.
- Be cautious of e-mails that claim to show pictures of the disaster areas in attached files because the files may contain viruses.
- Only open attachments from known senders. Make contributions directly to known organizations rather than relying on others to make the donation on your behalf to ensure contributions are received and used for intended purposes.
- Do not give your personal or financial information to anyone who solicits contributions: Providing such information may compromise your identity and make you vulnerable to identity theft.
Anyone who has received an e-mail referencing the above information or anyone who may have been a victim of this or a similar incident should notify the IC3 via www.ic3.gov.
New Text Message Scam
Customers have reported getting text messages from someone claiming to be from the bank. The text message requests that personal banking information be texted back to the alleged bank representative. The First does not send text messages to customers. Please do not give out any information via text messaging.
New Credit Card Scam
The callers do not ask for your card number; they already have it. This information is worth reading. By understanding how the VISA & Master Card Telephone Credit Card Scam works, you’ll be better prepared to protect yourself.
One of our employees was called on Wednesday from ‘VISA’, and I was called on Thursday from ‘Master Card’.. The scam works like this: Caller: ‘This is (name), and I’m calling from the Security and Fraud Department at VISA. My Badge number is 12460. Your card has been flagged for an unusual purchase pattern, and I’m calling to verify. This would be on your VISA card which was issued by (name of bank). Did you purchase an Anti-Telemarketing Device for $497.99 from a Marketing company based in ?’
When you say ‘No’, the caller continues with, ‘Then we will be issuing a credit to your account. This is a company we have been watching and the charges range from $297 to $497, just under the $500 purchase pattern that flags most cards. Before your next statement, the credit will be sent to (gives you your address), is that correct?’
You say ‘yes’. The caller continues – ‘I will be starting a Fraud investigation. If you have any questions, you should call the 1- 800 number listed on the back of your card (1-800 -VISA) and ask for Security.’
You will need to refer to this Control Number. The caller then gives you a 6 digit number. ‘Do you need me to read it again?’
Here’s the IMPORTANT part on how the scam works. The caller then says, ‘I need to verify you are in possession of your card’. He’ll ask you to ‘turn your card over and look for some numbers’. There are 7 numbers; the first 4 are part of your card number, the next 3 are the security Numbers that verify you are the possessor of the card. These are the numbers you sometimes use to make Internet purchases to prove you have the card. The caller will ask you to read the 3 numbers to him. After you tell the caller the 3 numbers, he’ll say, ‘That is correct, I just needed to verify that the card has not been lost or stolen, and that you still have your card. Do you have any other questions?’ After you say No, the caller then thanks you and states, ‘Don’t hesitate to call back if you do, and hangs up.
You actually say very little, and they never ask for or tell you the Card number.. But after we were called on Wednesday, we called back within 20 minutes to ask a question.. Are we glad we did! The REAL VISA Security Department told us it was a scam and in the last 15 minutes a new purchase of $497.99 was charged to our card.
Long story – short – we made a real fraud report and closed the VISA account. VISA is reissuing us a new number. What the scammers want is the 3-digit PIN number on the back of the card Don’t give it to them. Instead, tell them you’ll call VISA or Master card directly for verification of their conversation. The real VISA told us that they will never ask for anything on the card as they already know the information since they issued the card! If you give the scammers your 3 Digit PIN Number, you think you’re receiving a credit. However, by the time you get your statement you’ll see charges for purchases you didn’t make, and by then it’s almost too late and/or more difficult to actually file a fraud report.
FBI Warns of Rise in Phone-Based Scams
New threat: Phishing attempts that ask the victim to call their bank to reactivate a credit card, then provide a false phone number.
With consumers finally getting wise to phishing attacks, scammers are hitting the phones.
The U.S.. Federal Bureau of Investigation’s Internet Crime Complaint Center (IC3) warned Thursday that so-called “vishing” attacks are on the rise. These are scams where criminals send an e-mail or text message to a victim, saying there has been a security problem and the victim needs to call his or her bank to reactivate a credit or debit card.
“Upon calling the telephone number, the recipient is greeted with ‘Welcome to the bank of …’ and then [is] requested to enter their card number in order to resolve a pending security issue,” the IC3 said in its alert.
In the past few years, inexpensive VoIP (Voice over Internet Protocol) technology and open-source call-center software has made it inexpensive for scammers to set up phony call centers, paving the way for these new types of scams. Security experts say that vishing can be more effective than traditional phishing techniques — which direct victims to fake Web sites — because the voice-based attacks have not been as widely publicized.
A new vishing scam involves sending text messages to cell phones, instructing victims to contact the fake online bank to renew their accounts, the IC3 said.
Those who are unsure whether they have been targeted by this scam should look up the bank’s phone number and call the bank directly, the IC3 advises.
Operated in partnership with the FBI and the National White Collar Crime Center, the IC3 is a clearing house for Internet crime complaints.
Pretext Calling and Identity Theft.
Pretext calling is a fraudulent means of obtaining an individual’s personal information. Pretext callers may contact financial institution employees, posing as their customers, in order to access customers’ personal account information. These callers may also contact consumers at home, posing as employees from a financial institution. Information obtained from pretext calling may be sold to debt collection services, attorneys, and private investigators for use in court proceedings. Identity thieves may also engage in pretext calling to obtain personal information for use in creating fraudulent accounts.
Steps you should take to protect yourself against identity theft and pretext calling include:
Do not give personal information, such as account numbers or social security numbers, over the telephone, through the mail, or over the Internet unless you initiated the contact or know with whom you are dealing.
Store personal information in a safe place and tear up old credit card receipts, ATM receipts, old account statements, and unused credit card offers before throwing them away.
Protect your PINs and other passwords. Avoid using easily available information like your mother’s maiden name, your birth date, the last four digits or your social security number, your phone number, etc.
Carry only the minimum amount of identifying information and the number of credit cards that you need.
Pay attention to billing cycles and statements. Inquire of the bank if you do not receive a monthly bill; it may mean the bill has been diverted by an identity thief.
Check account statements carefully to ensure all charges, checks, or withdrawals were authorized.
Guard your mail from theft. If you have the type of mailbox with a flag to signal the box contains mail, do not leave bill payment envelopes in your mailbox with the flag up. Instead, deposit them in a post office collection box or at the local post office. Promptly remove incoming mail.
Order copies of your credit report from each of the three major bureaus once a year to ensure they are accurate. (A fee may apply)
If you prefer not to receive pre-approved offers of credit, you can opt out of such offers by calling 1-888-5-OPT OUT.
If you want to remove your name from many national direct mail lists, send your name and address to:
DMA Mail Preference Service
P.O. Box 9008
Farmingdale, NY 11735-9008
If you want to reduce the number of telephone solicitations from many national marketers, send your name, address and telephone number to:
DMA Telephone Preference Service
P.O. Box 9014
Farmingdale, NY 11735-9014
Banking Department Urges Caution when Cashing Cashier's Checks from People You Don't Know
There have been an increasing number of Pennsylvanians reporting that they are being defrauded by counterfeit cashier’s checks.
In general, the fraud unfolds like this: A consumer is part of a fairly large financial transaction with someone who generally says that they live outside of the United States. The types of transactions that have been reported include payments for large items purchased through online auctions, deposits for apartments, and fees for nanny services, for example.
The so-called “buyer” sends an official-looking cashier’s check to pay for the service. The consumer, then, takes the check to the bank and cashes it.
There are two ways the scam can unfold: In the first, the buyer sends a check for well over the amount of the purchase (with some excuse about why) and asks the consumer to immediately refund the difference once they’ve cashed the check. In the second, the buyer waits a day or two (but only a very short time) and makes some excuse for canceling the transaction and asks the consumer to wire all of the money back.
A similar scam suggests that the consumer has ”won” a lottery or other prize but must send some of the proceeds of the check back for some specific reason, like processing or taxes.
The counterfeit cashier’s checks are such good reproductions that they’re difficult to spot, even by experienced financial professionals. Despite the fact that the consumer’s bank cashes the check, it will not be honored when the bank presents it to the ”issuing” institution for payment. The bank then, requires the consumer to return the funds.
The problem is that, by the time the fraudulent check works its way through the banking system (which can sometimes take more than 30 days), the con-artist has already taken the consumer’s money.
You can protect yourself by:
- understanding that when cashing a cashier’s check, even though the bank has provided you with the money, you are responsible for the funds until your bank has received the proceeds from the institution which originally issued the check
- being cautious of transactions with people you don’t know who purchase items via cashier’s check
- avoiding any situation where someone pays more than the purchase price of an item and demands that the extra money be returned
- being suspect of any cashier’s check that just shows up in the mail, especially if it has a ”congratulations” letter attached
- holding any funds provided by cashier’s check from someone you don’t know for 30 – 45 days before using those fund, especially when you have any sense that the transaction is out of the ordinary
If you believe that you’ve been the victim of this type of scam, please call the Pennsylvania Attorney General’s office at (800) 441-2555, the U.S. Secret Service at (202) 406-5850, or the Pennsylvania Department of Banking at (800) PA BANKS.
FBI Fraud Alert Questionnair
The First encourages you to review this questionnaire about Fraud Scams. If you have any questions or can answer yes to any of the questions, please call us at one of our branches. Click here to see the questionnaire.
Fraudulent Emails Requesting Personal Information
Recently, many Americans have received a series of fraudulent e-mails, which direct recipients to websites where they are asked to verify sensitive personal information. The e-mails claim that the individual’s personal information is necessary to assist in the fight against terrorism or for some other purpose supposedly required by law. These e-mails are purportedly sent from several government agencies or include content related to government agencies including the Federal Deposit Insurance Corporation, the Office of the Comptroller of the Currency, the Securities Investor Protection Corporation and others. The websites to which the email recipients are directed are often very similar to, if not actual clones of official government sites.
The fraudulent e-mails are part of a scam known as “phishing.” Phishing is the fraudulent scheme of sending an e-mail to a user falsely claiming to be a legitimate company. The email attempts to con the user into surrendering private information that could later be used for identity theft. The e-mail directs the user to visit a Web site where they are asked to update personal information, such as name, account and credit card numbers, passwords, social security numbers and other information. The Web site, however, is bogus and set up only to steal the user’s information.
As part of the Treasury Department’s efforts to fight identity theft, we want to assure Americans that federal financial agencies do not communicate with consumers by e-mail requesting important personal information such as your name, account numbers, date of birth and social security number.
Consumers can protect themselves from this latest identity theft scam by following these useful tips, which were developed by the Federal Trade Commission:
- If you get an email that warns you, with little or no notice, that an account of yours will be shut down unless you reconfirm your billing information, do not reply or click on the link in the email. Instead, contact the company cited in the email using a telephone number or Web site address you know to be genuine.
- Avoid emailing personal and financial information. Before submitting financial information through a Web site, look for the “lock” icon on the browser’s status bar. It signals that your information is secure during transmission.
- Review credit card and bank account statements as soon as you receive them to determine whether there are any unauthorized charges. If your statement is late by more than a couple of days, call your credit card company or bank to confirm your billing address and account balances.
- Report suspicious activity to the FTC. Send the actual spam to uce@ftc.gov. If you believe you’ve been scammed, file your complaint at www.ftc.gov, and then visit the FTC‘s identity theft web site (www.ftc.gov/idtheft) to learn how to minimize your risk of damage from identity theft.
The Treasury and federal financial regulators are working hard to combat identity theft including the use of new tools in legislation recently signed by President Bush. But all consumers must take reasonable precautions in the use of their personal financial information in order to help prevent themselves from becoming victims of identity thieves.
ATM Safety Tips: When Using An ATM…
- Be aware of your surroundings, particularly at night.
- Consider having someone accompany you when using the ATM after dark.
- If you observe or sense suspicious persons nearby, do not use the ATM at that time. Or, if you are in the middle of a transaction, cancel the transaction. Leave the area and come back another time or use an ATM at another location.
- If you are approached by any person who asks you to do them a “favor” or tries to draw you into conversation, cancel your transaction and leave the area. Report the incident to us as soon as possible.
- When using the ATM at night, park close to the ATM in a well-lighted area and always lock your car.
- If the lights on or around an ATM are not working, don’t use it. Report it to us the next day.
- If you are using another financial institution’s ATMs and shrubs or trees block the view, select another ATM.
- If you are using a drive-up ATM, be sure passenger windows and doors are locked.
- To keep your account information confidential, always take your receipts with you.
- Don’t display any cash. As soon as you complete the transaction, pocket the money and count it later.
- Report all crimes to the police immediately.
- If your card is lost or stolen, report it to us immediately. Call 215-579-3400 Monday-Friday 8:30 am to 5:00 pm or 800-236-2442 after business hours.
- Be careful not to reveal your secret code (PIN). When you punch it in, use your body to “shield” the keyboard. Don’t carry your personal identification number with your card, and never attach it to your card.
Copyright © 1992 Bankers’ Hotline.
Originally appeared in Bankers’ Hotline, Vol. 2, No. 11, 2/92
If you have any questions about these security and fraud alerts, please feel free to contact the bank at 215-860-9100.